Most larger companies process hundreds, if not thousands, of outgoing payments every day. These payments are crucial for the business and must be handled accurately and punctually. Yet, as the number of payments increases, their management can become challenging, particularly when dealing with tens or even hundreds of bank accounts. Oftentimes, treasury and finance teams have to deal with yet another layer of complexity when they need to improve payment processes to protect themselves against payment errors, fraud, or making payments to sanctioned beneficiaries, which requires implementing payment process controls and other security measures.
In this article, we’ll talk about why it’s anyway critical to have secure payment processes in place, what threats your organization could be facing, and how treasury and finance can tackle payment security within their own scope of work while keeping processes as efficient as possible. As a bonus, we’ll provide a fraud risk management framework that can make dealing with process improvements less overwhelming.
Why are payment security and controls more relevant than ever before?
Financial scams are often directed towards treasury and finance teams, making these teams important stakeholders in payment security projects. In collaboration with IT and security professionals, they play a crucial role in ensuring payment security. According to a recent survey conducted by Trustpair, SAP, and Accenture, payment security also showed to be a topmost priority for finance and treasury professionals. With the increase in incidents of fraud and cyberattacks, companies can no longer ignore payment security. As a result, most teams are now actively reviewing their organizational processes to enhance safety. Shockingly, despite the topic gaining popularity, the survey also revealed that 56% of US-based companies had still fallen prey to payment fraud in 2022.
in 2022, 56% of US companies had still fallen prey to payment fraud.
Treasury & Risk survey commissioned by Trustpair & Giact
At the same time, the research study also revealed that treasurers expect banks and system providers to take an active role in the fight against fraud attempts. To meet this growing demand, many advanced payment and TMS vendors have developed solutions to enhance payment security.
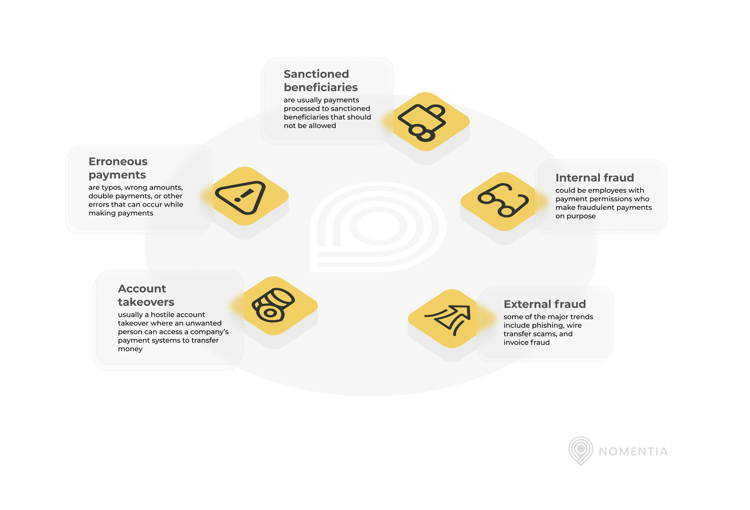
Differentiating between the types of payment issues that can occur
Even though some solutions provide the full suite of technical features for tackling payment errors, sanctions, and fraud, it is still important to differentiate between the security threats treasury and finance face because they require different approaches. Let's consider some of the most common threats that can occur:
- Erroneous payments: are typos, wrong amounts, double payments, or other errors that can occur while making payments.
- Sanctioned beneficiaries: are usually payments processed to sanctioned beneficiaries that should not be allowed.
- Internal fraud: could be employees with payment permissions who make fraudulent payments on purpose.
- External fraud: some of the major trends include phishing, wire transfer scams, and invoice fraud where criminals trick employees into paying them.
- Account takeovers: usually a hostile account takeover where an unwanted person can access a company’s payment systems to transfer money.
What belongs to payment security from a treasury and finance perspective, and how can you tackle it?
The question remains: what is really included in payment security from a treasury and finance perspective? And which threats can actually be fought by them? This can vary greatly depending on the organization, the experience of teams, and the policies treasurers have established regarding security, among other factors. Different treasury professionals may have different opinions on what payment security entails. However, we have noticed some common themes that treasurers at our clients focus on from a technological standpoint:
Avoiding erroneous payments
Manual processes are susceptible to errors, particularly when they are performed repeatedly, leading to handler fatigue. This commonly results in erroneous payments through typos, outdated vendor master data, or mixing up beneficiaries, for example. These errors can be compounded over time, resulting in time-consuming efforts to correct them, such as liaising with all involved stakeholders or seeking assistance from banks.
“Master data is critical for process continuity. Data are assets, and if we talk about master data, that is really a key asset, and you need to manage master data like you manage other key assets.”
Mark Roelands, Risk & Compliance consultant, grc consulting
An automated payment system, which is connected between your ERP and banks, can help you to keep your master data automatically updated and avoid outdated information. You can also avoid errors by setting up rule-based process controls or automated matching processes for reconciling financial records with bank statements. For larger single payment sums, a double verification by a second person can be helpful in preventing errors.
Ensuring payments aren't sent to any sanctioned beneficiaries
To comply with regulations and ensure security, most companies must check their payments against unwanted beneficiary lists. This can be achieved by verifying payments against public lists like OFAC's, EU's, and other institutions, as well as private blacklists or whitelists. As world politics continue to shift, these lists keep evolving, and hence, they need to be updated regularly.
Manual sanctions screening, i.e., uploading and downloading spreadsheets against sanction databases or manually searching lists each time a payment batch is processed, can take a lot of time. Therefore, our customers have found that sanctions screening is most suitable as an automated step of a payment process flow in a payments hub every time payments are executed.
Preventing fraudulent payments
Fraud is a recurring topic for many companies and is challenging to spot when hundreds of daily payments go out to various stakeholders. However, preventing fraud is critical as the losses can affect cash flow and liquidity planning. Organizations must tackle multiple types of fraud, each requiring a slightly different approach.
Some of the most common frauds are wire transfer scams, phishing, and fake invoicing. On the one hand, most of these derive from human vulnerabilities; hence, you should educate employees to identify such fraud. On the other hand, intelligent payment technologies can recognize some of these irregularities as they stand out from ordinary payments, by scanning vendor master data automatically, for example. And, of course, larger payment sums should always be verified by several people so that the financial loss cannot be too significant.
To avoid internal fraud, users should be given limited rights in payment processes, there should always be several people checking payments regularly, and the consequences of fraud should be made clear in treasury policies to avoid any ambiguity.
Ensuring that payment processes are standardized and creating company-wide visibility
Most companies we help have many local payment operations worldwide, where processes and systems can differ per location. This usually leads to a lack of transparency over processes and security, even the cash flow, on a group level.
In some cases, our customers want to centralize payments to a group-wide level and have global processes enforced, whereas in other cases, local entities still have more responsibilities. In almost all cases, companies want to use the same payment technology to tackle global payments, and the solution is rolled out country by country until all entities use the same system. A single system provides transparency into all payment-related cash flow, allows processes to be easily enforced, and allows users to be optimally managed. An additional benefit is that you can leverage payment technologies to streamline intercompany payments and payments in various currencies to minimize the associated costs.
Basic system security like SSO and MFA
One of the most crucial aspects of payment processing is controlling who can access your bank accounts or payment systems, how safe it is, and their rights to execute payments. Basic functionalities like multi-factor authentication (MFA) and single sign-on (SSO) are considered essentials by treasury professionals to keep their data safe and prevent unwanted logins. Typically, we see that companies require this for logging into payment technologies, and sometimes verification codes are even used when executing larger payment batches or sums.
User management and audit trail
One excellent control mechanism for security is user management. Once your treasury and finance team expand, with multiple entities and bank accounts, it becomes hard to have a bird's eye view of which users are managing what processes and what they should be allowed access to. Not to mention all the new joiners and people quitting the organization, which needs to be kept track of. Without central user management, it can quickly become overwhelming and time-consuming.
That's the reason why most companies look at tools for central user management, even integrated with HR systems to keep track of newcomers and leavers. A TMS, for example, allows admin users to easily assign roles or user rights to specific teams or individuals without giving them too few or too many permissions. For instance, group treasury can set permissions so that a local entity can access its own cash flows and execute local payments, but cannot access the data or payments of other entities or groups.
“to ensure safe practices, The principle of least privilege is a good rule of thumb: never give more rights to people in the system than the tasks they are actually performing according to their role.”
Tapani Oksala, head of partners, nomentia
On top of that, there's often a demand by the treasury and finance for audit trails. This means that organizations can see exactly what users do in systems in case something goes wrong (incidentally or on purpose) and review the logs afterward. This helps while planning any follow-up actions.
4 or 6-eye principles
A simple yet efficient way to ensure that something isn't wrong with a payment or payment batch is by including 4 or 6 eye principles into a payment process, for example, when a payment is about to be made. This way, a second or even third pair of eyes must verify the details of the payments being made to ensure they are correct. In payment hubs, you can set rules for when these principles should be applied, and the second reviewer will automatically receive a notification once their attention is requested.
Detect and respond notifications
Treasury and finance departments have a lot of tasks and processes to manage simultaneously. It can be hard to determine where their attention is needed most urgently. However, when attention is required, it is usually quite urgent. The same goes for payment security - if there is an issue, it is important that the relevant person is notified immediately. Although banks can notify users when there is a problem with a payment, this is only after the payment has been processed. Payment technologies can automatically identify almost any step in the payment process that requires attention and send notifications to the right user based on different sets of rules. This eliminates the need for emails to be sent back and forth between colleagues and other stakeholders. And if a payment anyway slips through, a hub can be integrated with the bank to ensure that the bank’s feedback is shown.
Payment matching or reconciliation
One of the most effective ways to prevent payment errors and fraud is by reconciling transactions with bank statements or invoices to ensure that all payments match payables. This is especially important when dealing with a large number of suppliers and payments. By using a system that can connect to your banks and ERP system, you can make sure that all necessary payment data is accurate and not missed. Such setups will greatly reduce errors related to manually going through each invoice and settling them.
However, payment security involves more than just technical solutions that are mentioned above. Other important topics that our partners and clients usually address include:
Employee awareness training
A big challenge for many companies is that fraud, errors, or scams start with an email or message to an employee via different channels. One important way to tackle this is to train employees, not just in treasury but in all teams, to identify scams. Most organizations do so through security awareness training that is usually initiated by IT and Security teams. Suppose something unwanted happens anyway; it's best to have the proper incident response procedures in place to tackle it immediately.
“Safe and secure culture is not being created by storing PDF documents with instructions on a sharepoint, it needs follow-up and training. Also, the company culture needs to be fostered in such a way that people feel comfortable stepping forward and point out things that aren’t in order.”
Mark Roelands, Risk & Compliance consultant, grc consulting
Treasury policies
One way to influence your payment security is by establishing the right payment-related policies that can be enforced company-wide. If they are easy to understand and can easily be followed without making processes inefficient, they can help ensure more secure practices.
Invoice approval procedures
Your invoice and vendor authenticity are important to keep the integrity of your payables. One way to avoid fraud, especially with invoicing scams posing a threat to organizations, is to ascertain that your invoicing procedures allow you to identify fraud quickly. Irregular payments, such as outside of approved countries, to new bank accounts, or irregular amounts, should always raise suspicion and be verified. In addition, you should encourage your team to ensure safety by cross-referencing vendor information when irregularities occur.
Incorporating these technical layers into the payment process is critical to efficient security against threats. On top of all technical security implementations, the human risk element should be tackled, which is sometimes an even bigger challenge as cyber threats and other scams continue to evolve and keep getting more challenging to identify for employees. Careful employee guidance and training should be a great first step in tackling that.
Where to start with payment security processes?
While facing the dual demands of optimizing payment processes cost-effectively and keeping security measures to mitigate financial losses from fraud and cybercrime efficient, organizations can find an effective solution in a payment factory. It's an approach that offers a combination of automation and process security, tackling both challenges simultaneously.
Still, it can be daunting for some to initiate implementing a new system, such as a payment hub, to address payment security concerns. Therefore, we advise to begin by examining your current processes and identifying areas that can be improved. If you discover that your current methods can only scale to a certain extent, it may be worthwhile to investigate the various technologies available on the market.
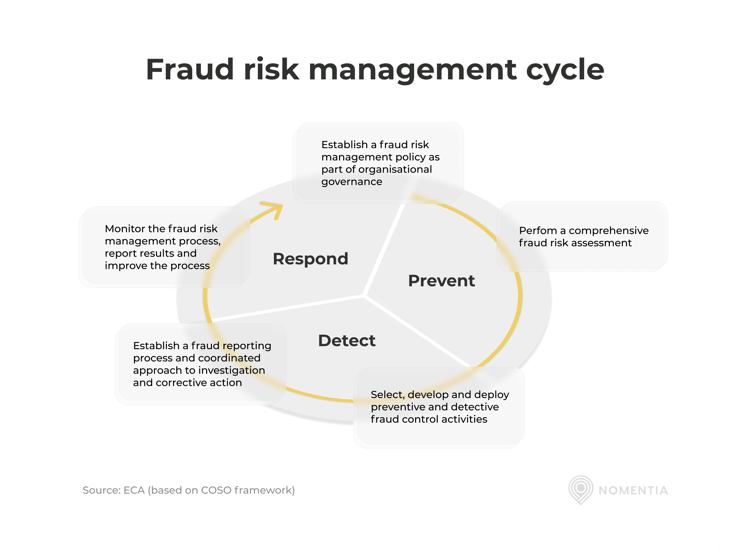
How a response framework can help in dealing with incidences
As your treasury and finance organization continues to work with payment security, it usually keeps identifying additional improvements. When dealing with multiple treasury processes, it can be difficult to determine which ones to focus on first. To simplify matters, you can follow a process framework like the fraud risk management cycle developed by the European Court of Auditors (ECA). It shows the need for establishing the right processes and policies, and running risk assessments, after which the right controls necessary can be developed to improve your current processes. As it is a continuous process, the process repeats itself constantly.
In addition, we always recommend you to spar with your payments system to improve processes, be it a bank, ERP, TMS, payment hub. Most of them have the necessary tools to help you fight payment threats better and more efficiently.



